You've just fallen for a phishing scam!
Don't worry, this was only a test. Emory IT sent this particular message to help educate people, but had this been a real phishing scam, you would have just given your password to a criminal.
Let's spend a few moments learning how to spot the signs of a scam and how to avoid others in the future.
Figure 1, below, shows the email message that you received as part of this test. It resembles a real Emory email, especially when you look at the addresses Do_Not_Reply@emory.edu (labelled with a "1") and http://leo.cc.emory.edu (labelled with a "2").
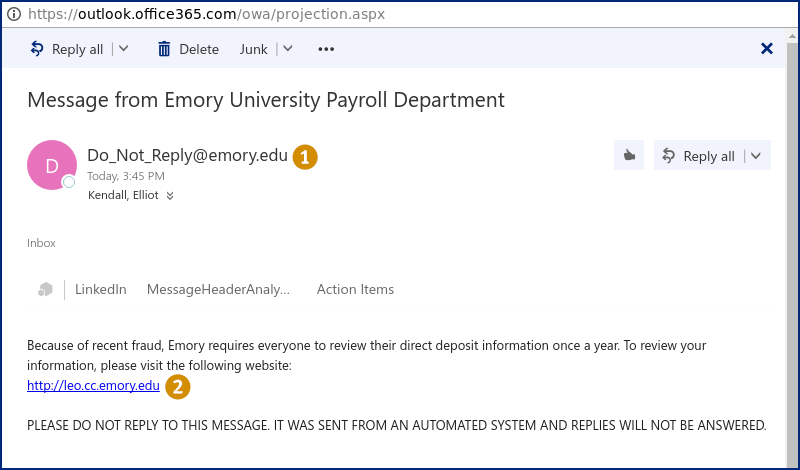
(1) is a valid Emory email address, but anyone can send email that appears to come from any sender. While (2) appears to be a valid Emory University link, it's not. As we will see next, it is possible to fake where links appear to go.
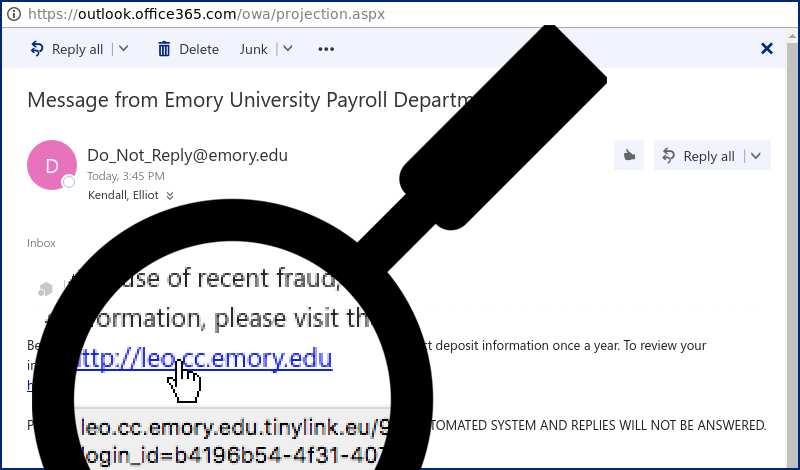
When you hover your mouse cursor over the link, you can see at (1) in Figure 2 that it actually goes to leo.cc.emory.edu.tinylink.eu/9b8198/?login_id= followed by some numbers. That is not a real Emory website.
The name of the website, which is the part right before the first slash, is leo.cc.emory.edu.tinylink.eu. It ends with .tinylink.eu, not .emory.edu. The phisher is trying to trick you by including emory.edu in the name, but only the last part of the name matters for telling you where the link really goes.
Hopefully, you saw that this was a scam before you clicked the link. However, even if you click the link, you have one more chance to figure it out before you fall for the scam. Here's the website that the link sent you to, overlayed with the real HR website. They look almost exactly alike! Let's examine them in detail, too.
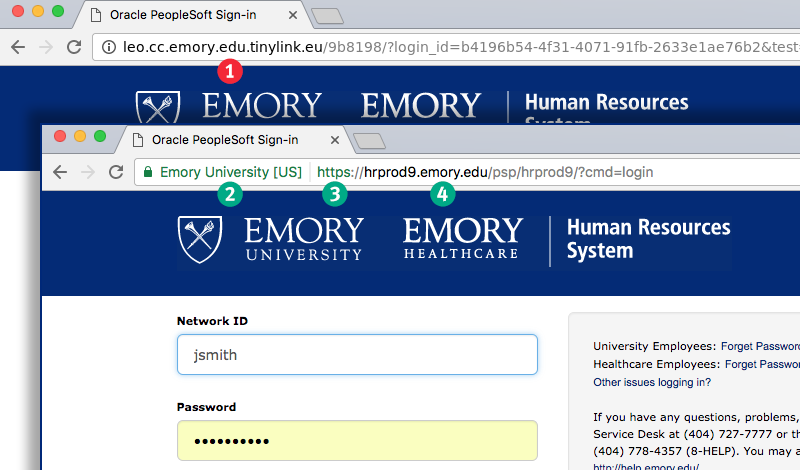
At (1) in Figure 3, you can see that same web address you saw when you hovered your mouse cursor over the link in the email. Again, the website name is the part before the first slash. In this case, it ends with .tinylink.eu rather than .emory.edu, so you know it's not a real Emory website.
At (2), you can see in green the words Emory University [US] in green text. Depending on which web browser you use, the design could look slightly different from Figure 3. Nonetheless, when you see a label like this to the left of the web address, it means that the website you are visiting belongs to the named organization.
Make sure you only trust the label if it appears to the left of the address. Criminals may include similar-looking text elsewhere in the page to try to confuse you. Not all legitimate sites have a label like this, but all sites with labels belong to the organization listed in the label.
At (3), you can see the text https://, which indicates you are using an encrypted website. You should NEVER enter a password, credit card number, or other sensitive information into a website whose address does not start with https://.
At (4), you can see the name of the website, hrprod9.emory.edu. Again, the website name is the part before the first slash. In this case, it ends with .emory.edu, so you know it is a real Emory website.
Thanks for taking the time to read through this tutorial. It could help protect you the next time a criminal tries to scam your work email.
